Cyber Risk may be new to you. This page is not intended to give you an all-inclusive picture of Cyber Risk but will introduce you to Cyber Risk Management and explain why we do what we do. We will tell you how Cyber Risk Management restored operational stability to a significant number of small and medium size businesses (SMBs) who had suffered a Cyber Security Event.
Cyber & Risk Solutions
What Is Cyber Risk Management?
Cyber Risk Management is an analytical approach that removes, mitigates, or transfers the risks associated with a company’s technology. As long as you employ any type of technology in your business you have a Cyber Security exposure. You are familiar with Risk Management in general and practice it every day. When you leave your house or apartment you practice all three core elements of Risk Management. Let’s use the Risk of theft or burglary as the example. First, when you leave your residence, you don’t leave all of your savings in the house or apartment, you keep it in a bank for safe keeping. By doing this, you remove some of your risk to loss of valuables by eliminating the possibility that someone breaking into your house or apartment will be able steal your entire savings. Second, when you leave your residence, you lock the door to help prevent someone from entering. By doing this you are reducing the chance of a burglary or mitigating the risk. Finally, even though you remove some of your risk and mitigate specific risk, most people still understand that it is important to buy insurance to protect against burglary should the mitigation attempts fail. When you buy insurance you are transferring your risk to another party, the insurance company. Cyber Risk Management is very much the same but requires a combination of unique skills to do it properly.
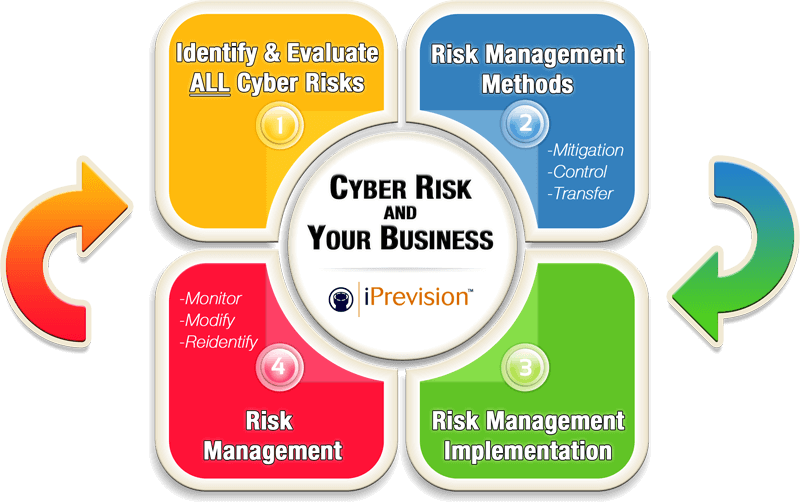
Does Cyber Risk Management Always Work?
No, Cyber Risk Management doesn’t always work unless all three elements are properly intertwined. Taking the analogy of your burglary protection a step further, if you placed your savings in the bank but failed to lock your door and failed to purchase insurance, if you had a burglary, although you wouldn’t lose the money in the bank, it would still be a very significant loss. If you choose to neglect any of the three areas of Cyber Risk Management, you shouldn’t expect your Cyber Risk Management program to work. Cyber Risk Management will work, does work and has worked for many organizations. This is not to say that you will be able to completely eliminate the chances of a Cyber event but, should a Cyber event occur, it won’t leave your business in a state that makes it difficult just to survive. A 2012 study by the National Cyber Security Alliance, found that 60 percent of small firms go out of business within six months of a data breach.
What Is the Real Threat to a Small & Medium Sized Business?
Cyber-attacks against SMBs rose significantly over the past few years, making them the fastest-growing group of targets. SMBs are facing the same cyber threats as large enterprises, but have a fraction of the budget to deal with them. Unlike big corporations with a large technical staff, the typical IT person or department at a small or midsize business wears many hats. Most SMBs lack strong security procedures and policies. Only about a third of small business owners have data security policies. Most cyber attackers follow the path of least resistance. In many cases, this means targeting the very businesses that can least afford to be hit. A small or midsize business is more likely – not less – to face a cyber-attack compared with large enterprises.
Our Process
We understand the Cyber Risk Cycle and more specifically, we know how important each of the phases are on their own. We also feel strongly about how important it is to understand the entire picture prior to moving forward. With this in mind, we specialize in the transfer portion of the cycle by providing cyber/network liability coverage’s that represent one of the three legs of the risk triad. What makes us very different from other insurance people is that we are highly technical and can truly understand what your current technology situation is, what mitigation elements are in place and based on that analysis, we determine the right level of risk transfer (cyber liability insurance) needed.
